This article delivers two key insights:
- Advantages of applying UK GDPR in research planning.
- Five approaches to safeguard data protection in lung cancer patient interviews.
Setting th Scene
The need of assessing the Quality of Life (QoL) in patients with lung cancer undergoing chemotherapy has been increasing. After treatment, patients may experience breathlessness or fatigue, along with potential challenges in their daily and occupational functioning. These side effects of chemotherapy consistently rank as a common complaint among patients. By using the validated QoL questionnaire from the European Organisation for Research and Treatment of Cancer, a hypothetical research project aim to summarize the QoL state among a cohort of patients in a hospital in the UK. Hopefully it can benefit the treatment of choice.
However, concerns regarding data protection were brought up in a management meeting, with the focus on data confidentiality.
Many patients consenting to participate in the study have uncertainty about their personal data processing, particularly in relation to sensitive questions. How do you lawfully and comprehensively tackle the data protection issue in a patient survey?
Data Governance in GDPR
To manage such risks, the GDPR can be one of the best solutions that is inetegrated into the research planning and implementations. Implementing this information governance rules can yield numerous benefits, encompassing aspects such as safeguarding individual rights and freedom, fulfilling lawful obligations, and gaining hospital’s competitive advantages.
Conversely, non-compliance with GDPR may cause research failure, distress to individuals, fines and penalties, and damage to hospital’s reputation.
Given GDPR’s seven key principles below, I propose five approaches that center on the principle of integrity and confidentiality to mitigate information governance risks and remove doubts regarding data security.
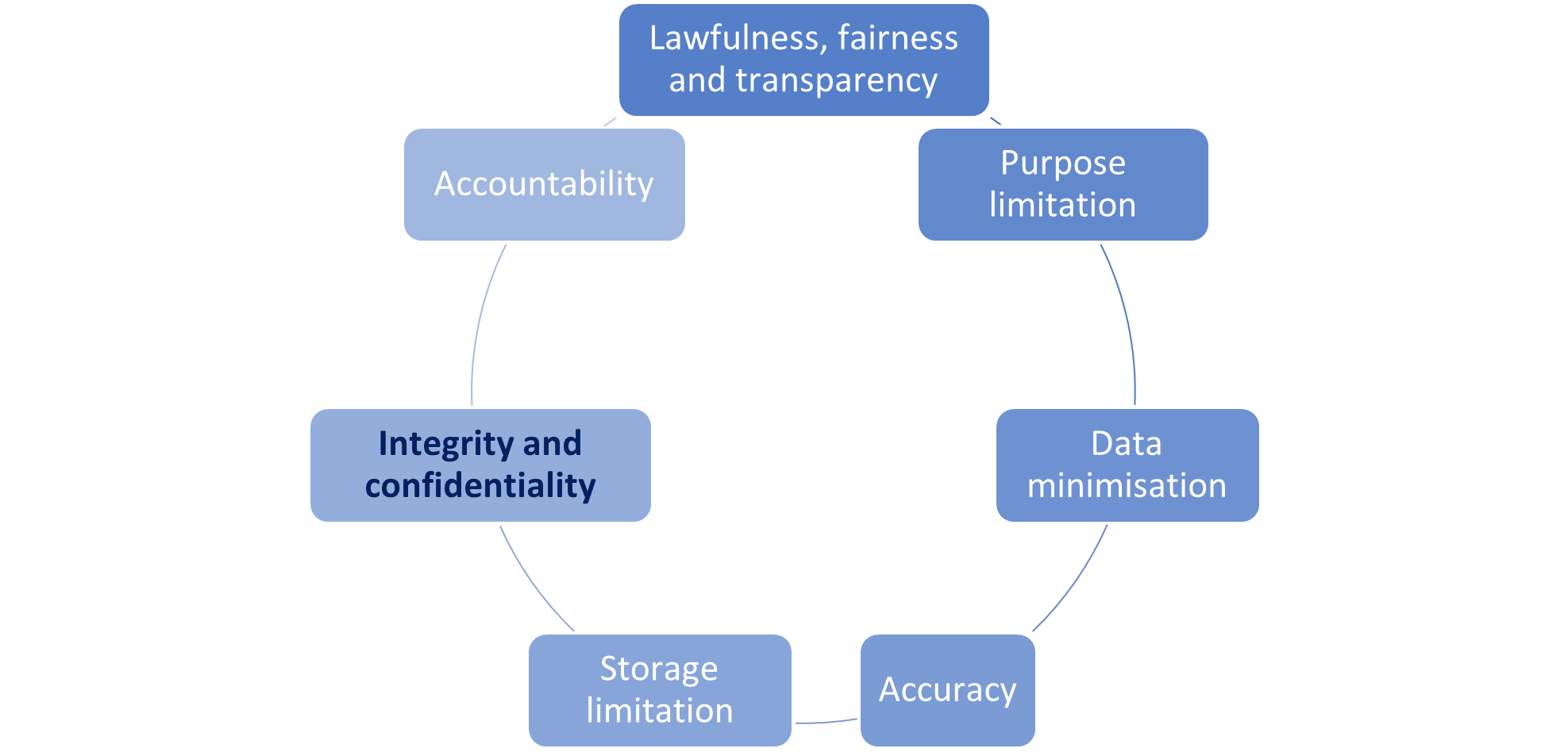
- Procedures and policy for data processing security
With regard to security in data processing, transfer, and storage, it can be achieved through technical procedures and organisational policy, such as encryption, pseudonymization, access control, and audit.
- Information technology (IT) security remediation
Through employing tools for reviewing IT security, system vulnerabilities can be identified and mitigated, along with fortified protection against potential security threats and cyber security events.
- Protocols for notifying a personal data breach
Protocols need to be developed to respond to a personal data breach event, ensuring that the investigation and reporting are completed within 72 hours.
- Appointing a data protection officer
This role’s responsibility is to oversee, monitor, and document operations related to data processing, applying extensive knowledge of data protection practices.
- A centralised area designated for data storage and processing
To minimize the risk of data leak, data processing is exclusively and physically performed on these dedicated desktops in an office.
For more detailed you can refer to the GDPR’s Data Protection and Impact Assessment Table in the end of this post
Recommended Approaches
To balance between risks presented by processing personal data and research utility, I propose endorsement of the first three approaches as a selection of strategies for this study due to following reasons. First, they follow GDPR’s principle of integrity and confidentiality, a priority particularly valued by your patients.
Second, the advantages inherent in these approaches are substantial. For instance, the first and second approach can minimize the likelihood of negative events, such as unauthorized access or data breach; the third approach then serves as a response to such negative events.
Third, the consequences of not implementing these approaches would be intolerable when weighed against their disadvantages, since a lack of robust safeguards for data protection can result in confidentiality risks, violation to regulations, and erode trust among patients.
Lastly, the estimated residual level of information governance risks (impact and probability) for the first three approaches are lower compare to the remaining approaches. A data protection officer (fourth approach) is considered more suitable for a large-scale study; a centralized area for data processing (fifth approach) runs a risk of accidental data corruption.
Conclusion
Research planning can incorporate GDPR to help make trade-offs in data/information governance risks. While each GDPR’s principle is equally important, I recommend three approaches that can strengthen the compliance to the principle of integrity and confidentiality. By establishing procedures and policy, implementing IT security remediation, and generating protocols for notification, this hypothetical study can have appropriate safeguards in place to process data safely.
Furthermore, I believe the assessment of QoL can provide the opportunity to improve QoL and symptom burden management of lung cancer patients with chemotherapy drugs. Therefore, we can not only accelerate research progress but also address confidentiality and regulatory requirements in our scope of research.
Data Protection and Impact Assessment Table
| What approach could be taken to reduce risk? | What actions would this involve? | What are the advantages and disadvantages of these actions for research? |
|---|---|---|
| Approach 1: Procedures and policy for data processing security | (1) Data processing involves the practice of protecting information from unauthorized access and corruption during the entire research lifecycle. (2)It encompasses robust encryption and pseudonymization of personal data, while in parallel ensuring confidentiality, integrity, and resilience of processing systems. (3)Regular audit and monitoring are required to promptly detect and address any anomalies or potential data breaches. (4)Encrypted data transfer is implemented, and data storage and network security are ensured through essential measures on physical hardware. | (1) Advantages: (1-1)Implementing security procedures and policies helps mitigate the risks of accidental or unlawful destruction, alteration, loss, and unauthorized access. (1-2)It not only complies with Article 32 of the GDPR but also adheres to the accountability principle of the GDPR, as the security logs and documentation can be used to demonstrate compliance. (2) Disadvantages: Enforcing access controls could introduce complexity and potentially decrease efficiency within the research project. |
| Approach 2: IT security remediation | (1)IT security remediation is an actionable set by detecting and protecting against potential security vulnerabilities or cyber security events, such as unauthorized access or disclosure due to non-encrypted transmission of data. (2)It identifies existing and scheduled mitigations for security issue, and rank likelihood of the issue occurring given existing or scheduled mitigations. (3)It updates existing security and antivirus software and strengthens IT infrastructure to ensure mitigations and controls are in place. | (1) Advantages: (1-1)Cybersecurity remediation can help manage risks and intercept IT security threats. This approach aligns with the National Cyber Security Centre (NCSC) Cyber Assessment Framework (CAF) guidance. (1-2)By identifying security concerns, it indirectly adheres to the integrity and confidentiality principle of the GDPR. (2)Disadvantages: Procurement and management of security software entails ongoing expenses. |
| Approach 3: Protocols for notifying a personal data breach | (1)In response to personal data breach, protocols and internal procedures should be well-planned, including pulling the facts, contain the breach, access the risk, and report it without delay, and act to protect affected patients. (2)After having become aware of personal data breach, the research team should notify the issue to the Information Commissioner, no later than 72 hours. (3)LSHTM’s Research Ethics Committees should also be notified when any breach of the study protocol or the principles of Good Clinical Practice has been identified. | (1) Advantages: (1-1)According to Article 33 of the GDPR, reporting a personal data breach in a timely manner (<72 hours) can avoid fine (up to £8.7 million or 2 per cent of turnover) and penalties. (1-2)It meets the principle of lawfulness, fairness and transparency, accountability, and integrity and confidentiality in the GDPR. (1-3)A comprehensive procedure can save time to respond to an event of personal data breach and communication strategy (Article 34 of GDPR). (2)Disadvantage: Documented protocols and procedures are needed, along with essential training sessions for the research team. |
| Approach 4: Appointing a data protection officer | (1)The data protection officer is designated on the basis of data protection laws (GDPR) and practices for confidentiality. (2)The data protection officer is involved in all issues which relate to the protection of personal data, including regular and systematic monitoring of data subjects. (3)The data protection officer manages and maintains records of data analysis logs, as well as input and output activities within the designated area. | (1)Advantages: (1-1)Compliance with regulations is regularly and systematically monitored, which aligns with the Article 37 of the GDPR and the principle of integrity and confidentiality and accountability of GDPR. (1-2)There is a contact point on issues relating to processing and protecting personal data. (2)Disadvantages: (2-1)The scope of this research is insufficient to warrant the role of a data protection officer, since systematic monitoring of data subjects is not conducted on a large scale. (2-2) Research budgetary allocation will be required to hire a data protection officer. |
| Approach 5: A centralised area designated for data storage and processing | (1)A structured set of personal data, including electronic health records, is stored in the filing system of the desktops in the information management department at the hospital. (2)Only members from the research have access to the research eligible patients’ personal data. (3)Data processing and analysis are exclusively and physically performed on these dedicated desktops. | (1)Advantages: (1-1)It ensures that data remains confined to these systems and cannot be exported, minimizing the risk of data leak. (1-2)It provides protection against unauthorised processing of personal data, which aligns with the principle of integrity and confidentiality from the Article 5 of the GDPR. (2)Disadvantages: (2-1)There is a risk of accidental loss or corruption in the event of destruction or damage to the area of centralized data. (2-2)Remote work is not available. |
In collaboration with ChatGPT, this article has been adapted from the assessment of the Thinking like a Health Data Scientist module at LSHTM.
